
Panda Endpoint Protection Plus
Simple and Light Endpoint Security and Productivity Solution
Panda Security is now a part of WatchGuard Technologies, please visit our WatchGuard Technologies website to learn more about this product!
Overview:
Manage the security of all the computers in your network and control user productivity at the lowest possible cost of ownership
Panda Security presents its simple and light endpoint security and productivity solution. Endpoint Protection Plus provides centralized and uninterrupted protection for all of your Windows, Mac and Linux workstations, including laptops and servers, in addition to the leading virtualization systems and Android devices.
Panda Security's Collective Intelligence technology protects all workstations and servers against threats and exploits that use unknown zero-day vulnerabilities in real time, without needing to install additional servers or IT infrastructures. It also monitors and filters Web traffic and spam, allowing the company to focus on its business and forget about unproductive employee behavior.
With Endpoint Protection, the protection is managed conveniently and easily from a single Web console, permitting centralized administration anytime and anywhere, without needing technical knowledge.
Keep any corporate network virus and spam free. Monitor your users' web access.
Endpoint Protection Plus provides centralized protection for all of your Windows, Mac and Linux workstations, including laptops, smartphones and the leading virtualization systems.
Why do I need an enterprise antivirus solution like Endpoint Protection Plus?
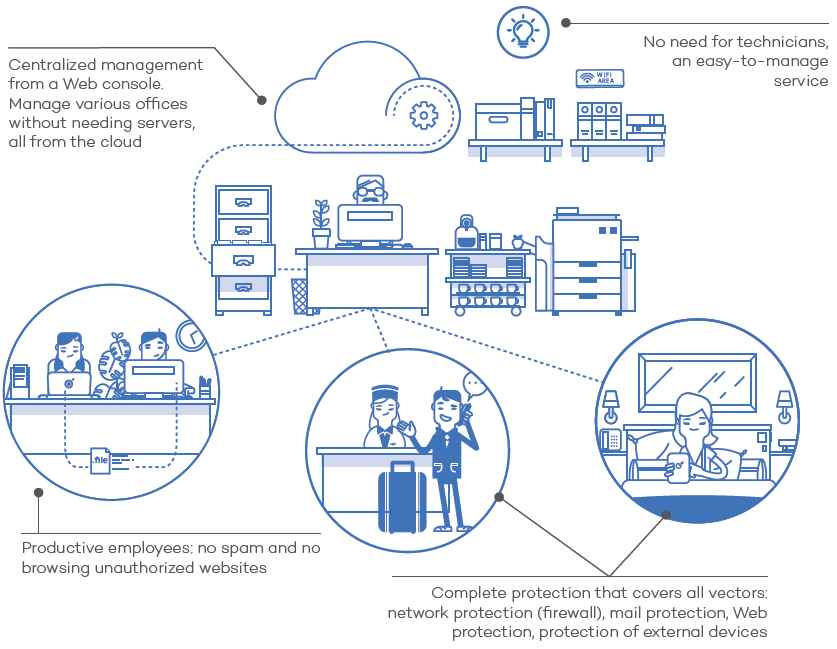
Centralized management from the cloud
All operations are performed in the cloud. Therefore, the impact of the antivirus on system performance is virtually zero.
![]() Cross-platform protection
Cross-platform protection
Endpoint Protection protects all of your computers running Windows, Linux, Mac OS X, in addition to Android smartphones and tablets, against known and unknown (Zero-Day) threats.
Minimizes maintenance costs
Our antivirus solution does not require additional infrastructure in your offices, minimizing the investment needed.
Real-time monitoring
Remotely monitor, control and adjust the security level of all network devices.
Features:
Protection and disinfection
- Proactive and real-time protection from the cloud thanks to Panda Security's Collective Intelligence.
- Maximum malware detection, even for malware that exploits unknown (zero-day) vulnerabilities, regardless of the source of infection (email, Messenger, Web, etc).
- Anti-theft protection for mobile devices through geolocation tools. We prevent confidential information from leaking from your company through remote data wiping and device locking.
Anti-spam and Web filtering
- No more saturated inboxes thanks to anti-spam protection and complete protection against malicious messages in Exchange servers.
- Monitoring and filtering of website categories that are unproductive and/or dangerous for your company during working hours, without needing to install add-ons on the user's browser.
Ease to use, easy to maintain
- Manage the security of all users from anywhere from the Web console.
- Simple, automatic and/or remote installation.
- Automatic or scheduled transparent updates to avoid any inconvenience to the user.
A level of security for each situation and environment
- Profile-based security to adapt the protection to the specific needs of your users.
- Centralized monitoring of the security status of all PCs, servers and laptops through comprehensive dashboards.
- Device control to block entire peripheral device categories (USB drives and modems, webcams, DVD/CD, etc.) with whitelists and control of permitted actions (access, read, write).
Benefits:

Simple and Centralized Security for all Devices
Centralized management of security and product upgrades through a simple Web browser for all network workstations and servers. Manage your Windows, Linux, Exchange Server, Mac OS X or Android protection from a single administration console.

Cleaner Monitor: Repair any Infected Computer
Run the Cleaner Monitor tool remotely and repair workstations infected with advanced or non-conventional malware.

Real-Time Monitoring and Reports
With Endpoint Protection Plus you can carefully monitor the security of your corporate network.
Automatically generate easy to interpret reports and graphs, or consult all of this data in real time through comprehensive dashboards.

Profile-Based Configuration
Assign different protection policies to users through configuration profiles.
Apply different levels of protection according to the profile of the user that connects to your corporate network.

Device Control
Avoid malware entry and data leaks by blocking device categories: USB memory sticks and modems, webcams, DVD/CD drives, etc.
In addition, you can establish exceptions with device whitelists, or simply block certain dangerous actions (access, read, write) on protected computers.

Flexible and Rapid Installation
Deploying the antivirus across complex networks has never been easier.
You can use two methods to install the antivirus on all endpoints on your network: via an email with a download URL or transparently with the Endpoint Protection Plus deployment tool (compatible with Active Directory, Tivoli, SMS etc.).

Malware Freezer
With Malware Freezer you can avoid any false positives. Freeze the malware detected for seven days and if it is a false alarm, automatically restore the file on the user's system.

No More Saturated Mailboxes
Reduce the risk of attacks on your Exchange servers with the content filter feature. Improve end-user productivity and protection by filtering unwanted and malicious messages with the anti-malware and anti-spam engines.

ISO 27001 and SAS 70 compliant. Guaranteed 24x7 availability
The solution is hosted on Microsoft Azure with complete data protection guaranteed. Our data centers are ISO 27001 and SAS 70 certified.
Technical Requirements:
| Technical Requirements | |
|---|---|
| Web Console |
|
| For Workstations and File Servers |
|
| For Exchange Server |
|
| For MAC Workstations / File Servers |
|
| For Linux Workstations / File Servers |
|
| For Android devices |
|
| Supported Virtualization Environments |
|
Compare:
| Adaptive Defense 360 | Adaptive Defense | Endpoint Protection | Endpoint Protection Plus | Systems Management | Fusion | Fusion 360 | |
|---|---|---|---|---|---|---|---|
| Protection | |||||||
| Protection against known and zero-day malware | |||||||
| Protection against known and zero-day ransomware | |||||||
| Protection against known and zero-day exploits | |||||||
| Anti-spyware, anti-phishing protection, etc. | |||||||
| Protection for multiple attack vectors (Web, email, network, devices) | |||||||
| Traditional protection with generic and optimized signatures | |||||||
| Protection against Advanced Persistent Threats (APT) | |||||||
| Managed service: Classification of 100% of applications before execution (1*) | |||||||
| Managed service: Threat Hunting (2*) | |||||||
| Queries to Panda’s cloud-based collective intelligence | |||||||
| Behavioral blocking and IoA detection | |||||||
| Personal and managed firewall | |||||||
| IDS / HIDS | |||||||
| Ability to block unknown and unwanted applications | |||||||
| Device control | |||||||
| URL filtering by category (Web browsing monitoring) | |||||||
| Content, Virus and Spam filtering for Exchange Server | |||||||
| Built-in antivirus protection for Exchange Server | |||||||
| Built-in anti-spam protection for Exchange Server | |||||||
| Monitoring | |||||||
| Advanced endpoint security | |||||||
| Cloud-based continuous monitoring of all process activity | |||||||
| Data retention for one year for retrospective attack investigation | |||||||
| Detection | |||||||
| Detection of compromised trusted applications | |||||||
| Managed service: Classification of 100% of applications during and after execution (1*) | |||||||
| Fully configurable and instant security risk alerts | |||||||
| Containment | |||||||
| Real-time computer isolation from the cloud console | |||||||
| Response and remediation | |||||||
| Ability to roll back and remediate the actions committed by attackers | |||||||
| Centralized quarantine | |||||||
| Automatic analysis and disinfection | |||||||
| Investigation | |||||||
| Managed service: Threat Hunting (2*) | |||||||
| Incident graphs and lifecycle information available from the Web console | |||||||
| Ability to export lifecycle information for local analysis | |||||||
| Advanced Visualization Tool (add-on) | |||||||
| Discovery and monitoring of unstructured personal data across endpoints (add-on) | |||||||
| Attack surface reduction | |||||||
| Information about each computer's hardware and software components | |||||||
| Information about the Microsoft updates installed on endpoints | |||||||
| Real-time information about the status of all protections and communications | |||||||
| Unattended, automatic updates | |||||||
| Automatic discovery of unprotected endpoints | |||||||
| Ability to immediately protect unprotected endpoints remotely | |||||||
| Panda native proxy to support endpoints with no Internet connection | |||||||
| Endpoint security management | |||||||
| Centralized cloud-based console | |||||||
| Settings inheritance between groups and endpoints | |||||||
| Ability to configure and apply settings on a group basis | |||||||
| Ability to configure and apply settings on a per-endpoint basis | |||||||
| Real-time deployment of settings from the console to endpoints | |||||||
| Security management based on endpoint views and dynamic filters | |||||||
| Ability to schedule and perform tasks on endpoint views | |||||||
| Ability to assign preconfigured roles to console users | |||||||
| Ability to assign custom permissions to console users | |||||||
| User activity auditing | |||||||
| Installation via MSI packages, download URLs, and emails sent to end users | |||||||
| On-demand and scheduled reports at different levels and with multiple granularity options | |||||||
| Security KPIs and management dashboards | |||||||
| System status reports at different levels and with multiple granularity options | |||||||
| Device inventory and audits | |||||||
| Agent and agentless monitoring of devices | |||||||
| Patch management | |||||||
| Centralized software installation | |||||||
| Non-disruptive remote access | |||||||
| Remote Desktop | |||||||
| Built-in chat | |||||||
| Task automation and scripting | |||||||
| Component store - ComStore | |||||||
| Ticketing/Help Desk | |||||||
| Modules | |||||||
| Panda Data Control integration | |||||||
| Advanced Reporting Tool integration | |||||||
| SIEM integration | |||||||
| Panda Patch Management | |||||||
| Panda Full Encryption inregration | |||||||
| High availability service | |||||||
| Host platform certifications | ISO27001, SAS 70 ISO27001, SAS 70 | ISO27001, FISMA, SAS70, PCI DSS | |||||
| Supported operating systems | |||||||
| Supports Windows | |||||||
| Suppots Exchange | |||||||
| Supports macOS X | |||||||
| Supports Linux | |||||||
| Supports Android | |||||||
| Supports iOS | |||||||
| Support for virtual environments - persistent and non-persistent (VDI)** | |||||||
* Panda Fusion is a bundle of Panda Endpoint Protection Plus and Panda Systems Management. Panda Fusion 360 is the combination of Panda Systems Management and Panda Adaptive Defense 360 that are sold separately
** Compatible systems with the following types of virtual machines: VMWare Desktop, VMware Server, VMware ESX, VMware ESXi, Citrix XenDesktop, XenApp, XenServer, MS Virtual Desktop y MS Virtual Servers. Panda Adaptive Defense 360 & Panda Fusion 360 solutions are compatible with Citrix Virtual Apps, Citrix Desktops 1906 & Citrix Workspace App for Windows, Panda Securtity has been verified as Citrix Ready partner.
1* 100% Classification Service.
2* Threat Hunting and Investigation Service
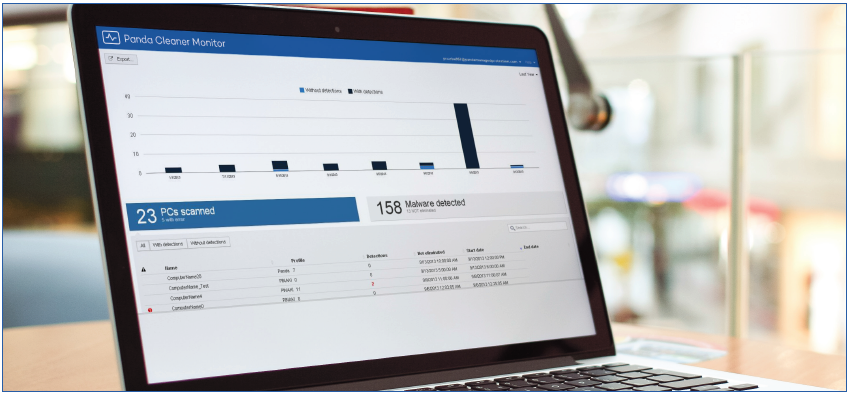
Cleaner Monitor:
Do you think your network could be infected, even though your antivirus tells you otherwise?
This is an advanced disinfection tool that runs a complete scan based on Collective Intelligence or cloud scanning in order to eliminate malware that traditional antivirus products are unable to detect. The benefits of having 25 years' experience detecting and disinfecting malware have enabled us to develop a solution that can monitor all the scans on your network and eliminate any latest generation viruses detected, remotely and from a centralized point.
![]()
Latest Technology
Includes the latest technologies, which are more aggressive than conventional antivirus solutions in detecting and disinfecting latest threats.
![]()
Automatic Reset
Cuts out the manual tasks of restoring infected systems, automatically undoing the changes made by malware to operating systems and restoring system policies.
![]()
Central Monitoring
Stores all scan and disinfection results in a single cloud-hosted repository for all computers on the network. Access it through a simple Web browser and get the information that you need.
Compatible Con:
- Windows 8 (32 and 64-bit)
- Windows 7 (32 and 64-bit)
- Windows Vista (32 and 64-bit)
- Windows XP SP2 or later (32 and 64-bit)
- Windows 2000 Professional
- Windows Server 2003 (32 and 64 bits)
- Windows Server 2008
- Windows Server 2008 R2
- Windows Server 2012 (32 and 64 bits)
Documentation:
Download the Panda Endpoint Protection Plus Datasheet (.PDF)

